Secure Your Shared Assets With Zero-Trust Security
As organizations continue to move away from the traditional on-prem environment and toward this new IT reality, their legacy cybersecurity solutions have been unable to keep up, creating unmanageable complexity and increased risk. These emerging issues lead to the implementation of Zero-Trust security architectures that do not automatically extend trust regardless of whether a user is inside or outside the perimeter.
The brief discusses how IT managers can deploy Zero-Trust security architecture:
- With micro-segmentation to isolate resources within the IT infrastructure.
- Divided network resources at a granular level and tune security settings to different traffic types.
- Policies that limit network and application flows to only those explicitly permitted.
This approach allows security teams the flexibility to apply the right level of protection to a given workload based on sensitivity and value to the business. It also helps mitigate risks from increasing access needs.
In today’s businesses, access typically isn’t limited to just employees and business partners — in many cases, it must also be extended to consultants, customers, suppliers, and more. These individuals all need access to business applications and IT resources in global private data centers and public clouds.
With fluid network perimeter and IT-enabled workforce, IT managers are challenged to provide reliable and secure mobile and global connectivity while overcoming shortcomings of traditional VPNs and software-defined perimeters.
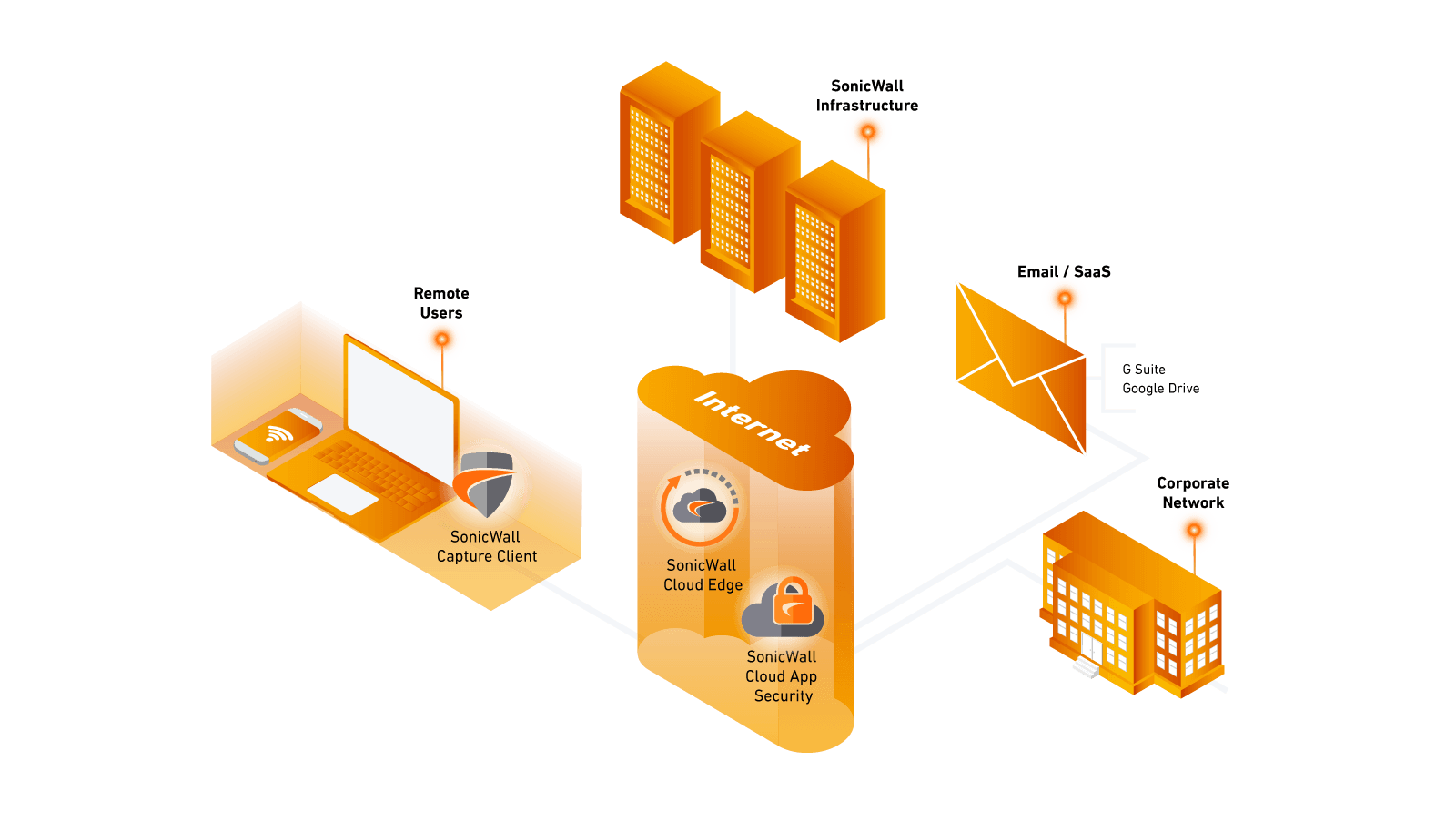
SonicWall Cloud Edge Secure Access offers an advanced Zero-Trust Network Access service delivered from the cloud and controlled through a single management console. Mobile employees are protected with Secure Access’ Single Sign-On native client applications that can be used on any Windows, Mac, iPhone, and Android device. With centralized control and identity management integrated into the Cloud Edge Secure Access portal, employees and groups can be easily added to corporate network resources and cloud environments with secure policy-based resource access. Detailed descriptions and applications for this solution are outlined in the full report.

- Deploy what works for you — where it works for you.
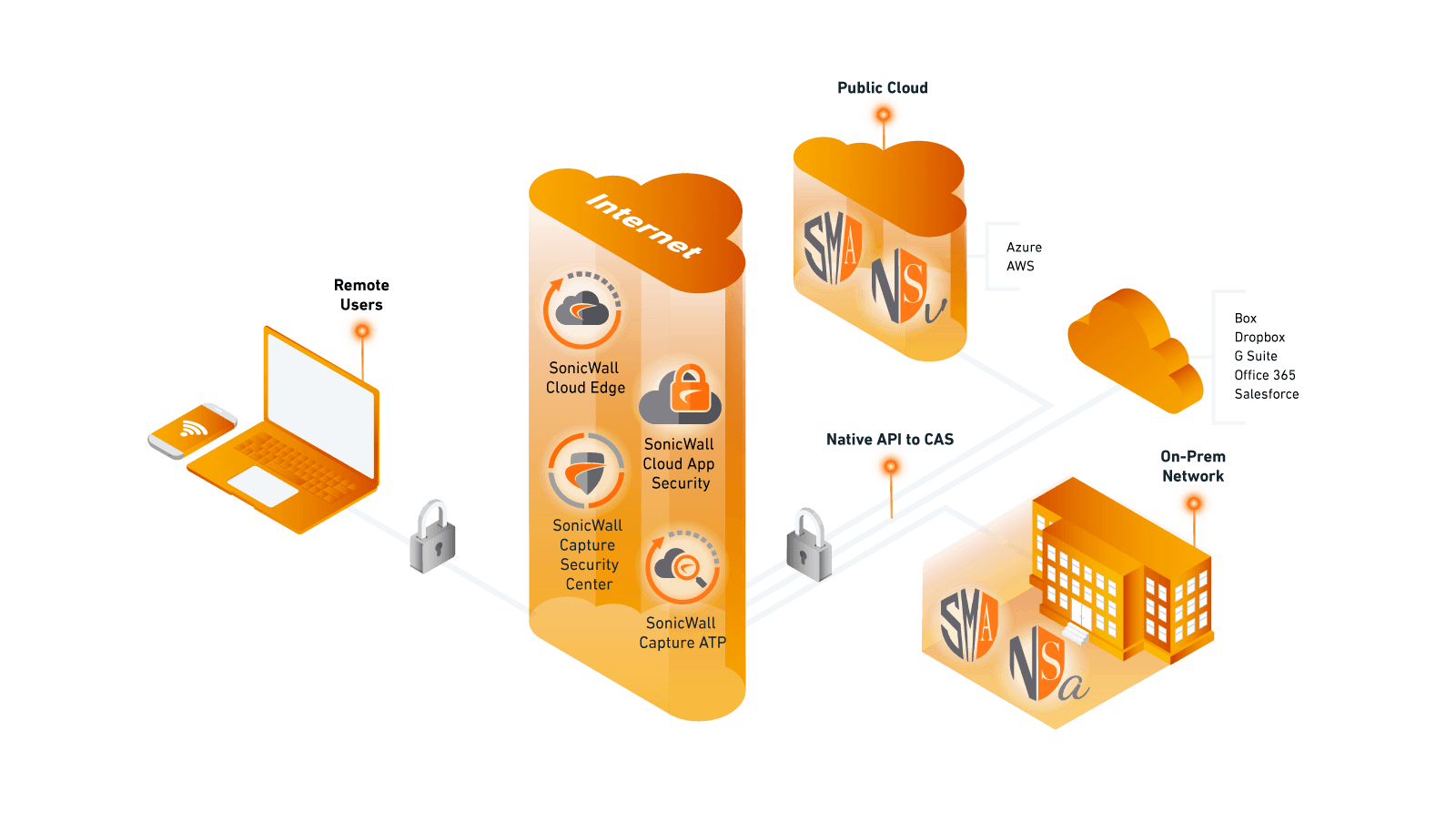
By providing on-premises, cloud-based and as-a-service options, SonicWall helps you deploy what works for your architecture and evolve secure cloud adoption at your pace. - Solve security and connectivity challenges for cloud-native and hybrid environments.
Mix and match security products to create or enhance cloud-native and hybrid deployment models that fit your current needs and bridges a path to a more virtualized reality. - Secure access to cloud and on-premises applications and virtualized workloads.
Leverage modern zero-trust capabilities to easily and quickly connect remote users to on-premises resources, cloud-hosted applications, branch offices and public clouds — all without installing hardware. - Protect distributed and remote workforces.
Safeguard remote employees and mobile workers with virtualized security options. Easily deploy security across multiple locations — with minimal IT support — using Zero-Touch Deployment capabilities. - Reduce costs and downtime.
Manage remote users, devices and applications from anywhere in the world. SonicWall’s cloud-native architecture eliminates the need to service physical appliances, schedule downtime and build out expensive redundancies. - Collaborate securely in a cloud-first world.
Secure common SaaS applications with a single security tool that requires no hardware or software installation. Quickly protect users, regardless of location, with convenient API connections to business-critical SaaS applications, including G Suite, Office 365 and more.
Mix & Match Architecture
Protect your organization, networks, users and devices on your terms. Explore real-world use cases that showcase the power and flexibility of scaling proven security across even the most complex cloud-native and hybrid environments.
Secure access to cloud and on-premises applications and virtualized workloads through modern zero-trust capabilities.
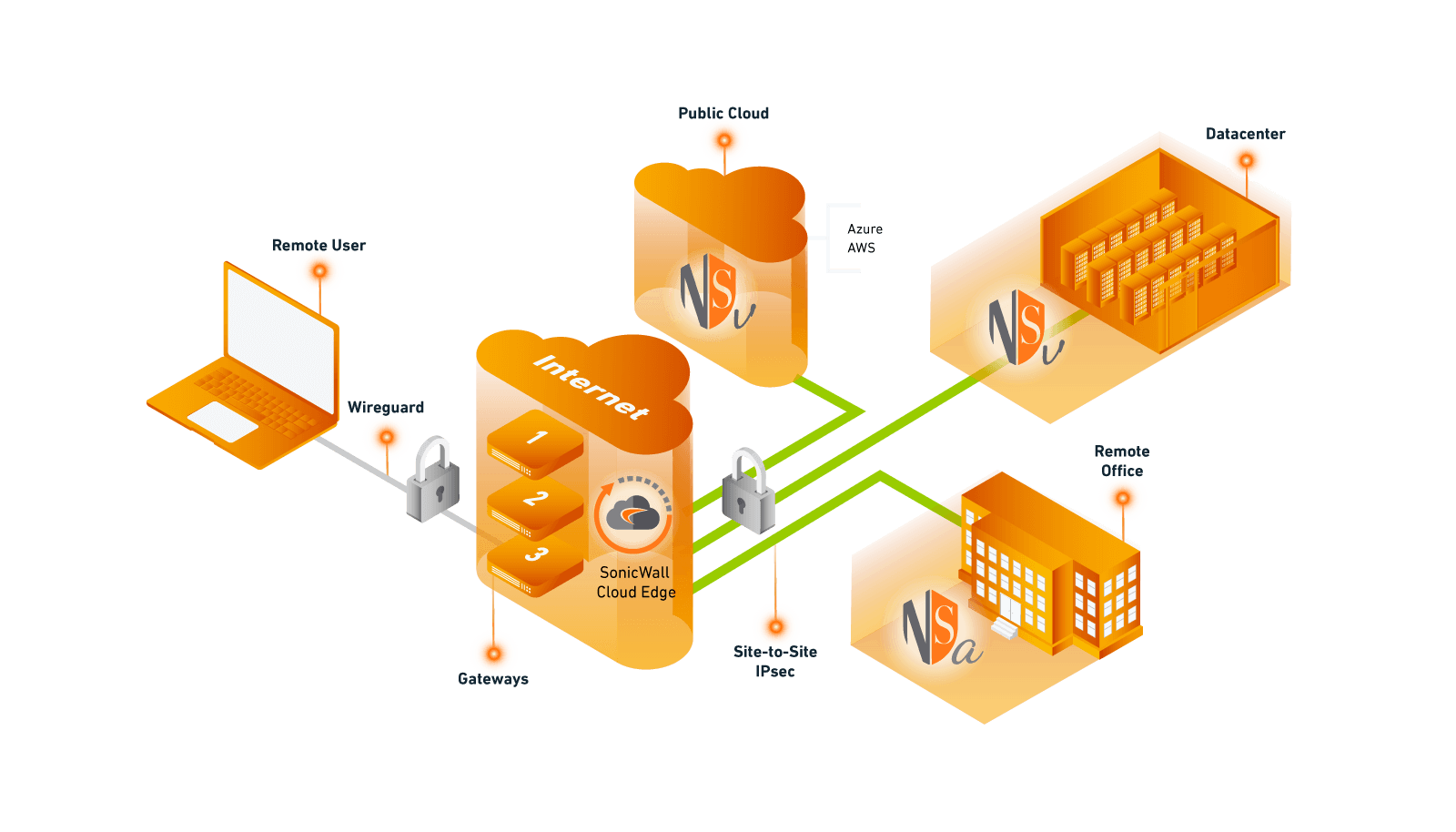
Products Used: Virtual Firewall, Physical Firewall, Cloud Edge Secure Access
Never trust. Always verify.
In less than 15 minutes, SonicWall Cloud Edge Secure Access quickly scales security beyond your perimeter through modern zero-trust principles. Establish logical trust zones to securely authenticate every user, device and location for access only to the specific services and resources required.