Empower, Enable & Protect Remote Workforces Outside the Traditional Perimeter
Remote work, the growth of BYOD, employee mobility, and the use of cloud-based applications are all on the rise, and perimeter-based security just isn’t enough to protect your enterprise in this new, hyper-distributed era. SonicWall believes that security perimeter must follow wherever humans work and extend to wherever the assets reside.
Zero Trust Access (ZTA) is the next-generation security approach that is made for the cloud era, and will become the standard of tomorrow’s secure access.
Cloud Secure Edge, Delivered as a Service
Deploy converged security and networking in the cloud to eliminate upfront costs and integration hassles. Control and protect network access to both managed and unmanaged devices based on identity, location and device parameters with Cloud Secure Edge, SonicWall’s robust Secure Access Service Edge (SASE) offering that delivers advanced, real-time zero-trust security.
SMA 1000 Appliance
Leverage SonicWall's globally trusted SMA 1000 Series to implement advanced Zero-Trust Access. Choose between an physical or a virtualized appliance to apply granular policy-based Zero-Trust control to define which users or devices can sensitive networks or resources - and which cannot.

Features & Benefits
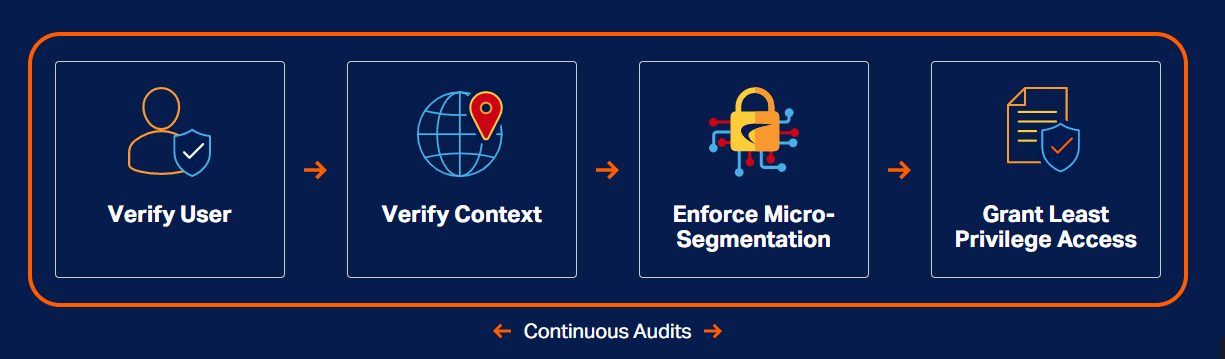
Verify User & Device Identities
ZTA stringent verification is based on user credentials, access time and device compliance to allow fast, simple access to business applications and data.
Least-Access Privilege Policies
ZTA removes excessive implicit trust. Users can only access what is needed to do their job, and nothing more, no over-privileged users are allowed.
Micro-segmentation
Use micro-segmentation to define internal trust boundaries and granularly control traffic flow to secure the infrastructure by reducing the attack surface and preventing threats from spreading laterally.
Always-On Application
Reconnect a user or device to the application or a set of applications without re-login and re-authentication.
Configuration Simplicity
Support easy-to-configure access policies. One single policy manages users, devices, applications, data and networks.
Modern Authentication Support
Add broad support for Identity Providers (IdP), SAML-based single-sign-on (SSO) and multifactor authentication (MFA) services from Okta, OneLogin, G Suite, Azure and Duo Security.
Monitor User & Device Continuously
Continuously monitor user and device behaviors, with enforcement applied during each login, or after a set period. It is entirely customizable.
Managed Device or Unmanaged BYOD
Increase productivity through diverse device support for various mobile devices and agent-less browser access from any public devices.
Zero-Trust Process
SonicWall Cloud Edge Secure Access provides secure remote access with cloud-native solutions. Least Privilege access allows organizations to secure sensitive resources by only giving trusted users access to what they need and reducing the lateral movement of threats throughout a network.